for IP Protection


LegalTech-Solution

in the digital age
.Accompany organizational, administrative and development processes in a tamper-proof and legally secure manner
bc2ip enables (intrinsically) the restriction of access to certain data and thus the restriction of the information flow, as well as the assignability of the previous information flow. Restriction of access and use represents one of the most important measures within the framework of information protection according to the European Trade Secrets Regulation (EU 2016/943).
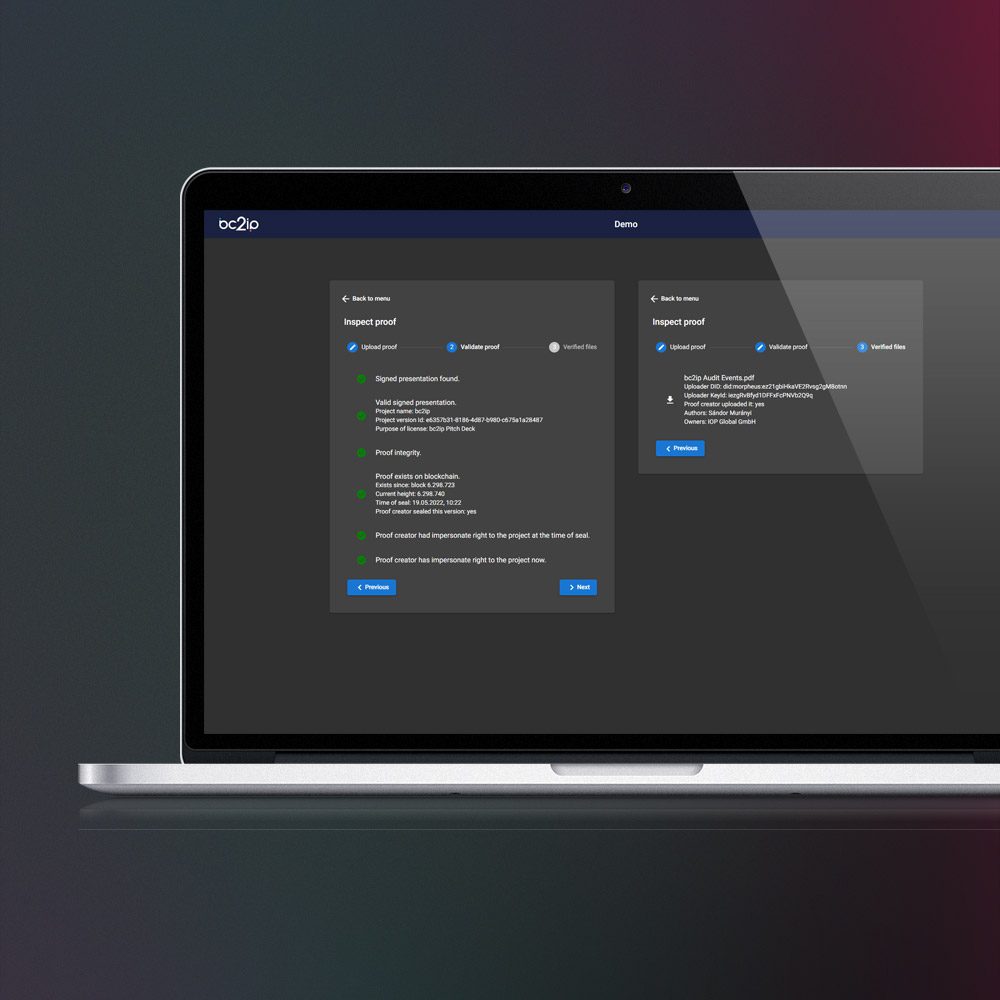
All digital processes taking place in bc2ip can be monitored and documented in an evidence-proof manner.
.Protection of Copyrights, trade secrets and contract documentation
Legal disputes over intellectual property and the requirements for protecting business secrets are constantly increasing. This is not only about patents. Individual project steps of technical and/or non-technical processes are covered with the help of bc2ip:
- Tamper-proof
- Full and complete documentation
- Secured by Proof of Priority
- Satisfies US and EU trade secrets regulations
.News & Blog


BLOG
EUR 223 billion in economic damage per year in Germany alone
Patent infringements (even before registration), legal disputes relating to IP rights, the failure, theft, or damage to information systems, and theft and industrial espionage of business and trade secrets lead to ...
.bc2ip testimonials
„With bc2ip, we can quickly offer our clients legally resilient and cost-effective options for prevention in case of a dispute. bc2ip can digitally protect know-how! This is the new road to innovation.”
Patent Attorney Dr.-Ing. Jörg Wagner – trierpatent®


Protecting your Intellectual Property
The path to intellectual property rights can sometimes be full of challenges and obstacles and is increasingly collaborative.Stakeholders exchange data throughout the process. This harbors risks to data and information—the solution: bc2ip
The bc2ip app creates a secure environment for all parties and opens up a new form of procedural collaboration for you.
The bc2ip app creates a secure environment for all parties and opens up a new form of procedural collaboration for you.


Effectively document and protect trade secrets
The European Trade Secrets Regulation (EU 2016/943) states that a "trade secret" must be protected by "reasonable measures to preserve the secrecy." Otherwise, a trade secret is not covered by the respective national laws.
"bc2ip enables the implementation of various technical and organizational measures and monitoring capabilities to protect your trade secrets."
Johannes Hagebölling
Attorney at law
"bc2ip enables the implementation of various technical and organizational measures and monitoring capabilities to protect your trade secrets."
Johannes Hagebölling
Attorney at law
.Our mission is to provide the most effective protection for your intellectual property, ideas, and processes.
.Problem & Solution
Theft
Theft of business and trade secrets causes high economic damage (Germany 220 billion euros p.a., source KPMG)
Protection
Effectively protect trade secrets in a cryptographically secure digital data environment.
Legal disputes
Intellectual property (IP) disputes are on the rise. The verifiability of information flows and the respective knowledge of individual participants can often be decisive in disputes.
Evidence
Gain legal certainty with forgery-proof and verifiable evidence.
Documentation
Lack of process reliability due to complex documentation processes.
Process reliability
Efficient process reliability is established with the help of automated, seamless, tamper-proof, and legally secure documentation.
.Four reasons for bc2ip
Create authenticity
Proof of persons, devices, and individual attributes using decentralized identifiers (DIDs) and verifiable credentials (VCs): Who did what, when, and with what?
01


On-premises solution
Optimizing access security is ideally suited for implementing the legal requirements of the Trade Secrets Protection Act.
02


Time stamping near real-time
Tamper-proof timestamping on the blockchain takes place within just 12 seconds.
03


Cross-industry
bc2ip is equally applicable for industrial, research, and service companies. bc2ip creates a new standard in the evidence of events.
04