Industries
- Home
- Industries
.Innovative LegalTech solution for industrial, research, and service providers
bc2ip sets new standards in the documentation and verifiability of digital processes across industries. It enables industrial, research, and service companies to design their organizational, administrative, and development processes in a tamper-proof, evidential manner.
Law firms
.Innovative White Label Blockchain LegalTech Solution for Intellectual Property Protection
With bc2ip you provide your law firm and your clients with a digital data room for all kinds of product development processes, patent applications, creation processes of works, trade secrets, and contracts.
All digital processes can be monitored and documented in an evidential and tamper-proof manner. With the help of DIDs and timestamps, bc2ip enables the evidentiary consistency, integrity, and personal assignment of digital information of all entities involved in the process.
.With the LegalTech solution bc2ip, specially developed for IP lawyers and law firms, you can launch your law firm processes into the digital age.
Enterprises
.Blockchain technology for enterprise business process management
bc2ip provides a digital data space for all kinds of digital assets, e.g., product development processes, patent applications, creation processes of works, trade secrets, and contracts.
The European Trade Secrets Regulation (EU 2016/943) states that a “trade secret” must be protected by “reasonable measures to preserve the secrecy.” Otherwise, a trade secret is not protected by the respective national laws.
„bc2ip enables the implementation of various technical and organizational measures, as well as their monitoring, to protect your trade secrets and thus provides the basis for compliance with the German Trade Secrets Protection Act (GeschGehG).”
Attorney at law Johannes Hagebölling
.bc2ip usecases:
.Cooperation and collaboration:
Agile companies and their developers share data on the way to industrial property rights or new cooperation partners. This is where risks lie dormant.
bc2ip makes it possible to develop ideas in a protected manner across the company jointly
and at the same time, work together confidentially and legally.
Individual project steps of technical and non-technical IP processes can be seamlessly documented, especially for protecting copyrights, trade secrets, and invention contributions.
.Corporate Workspace:
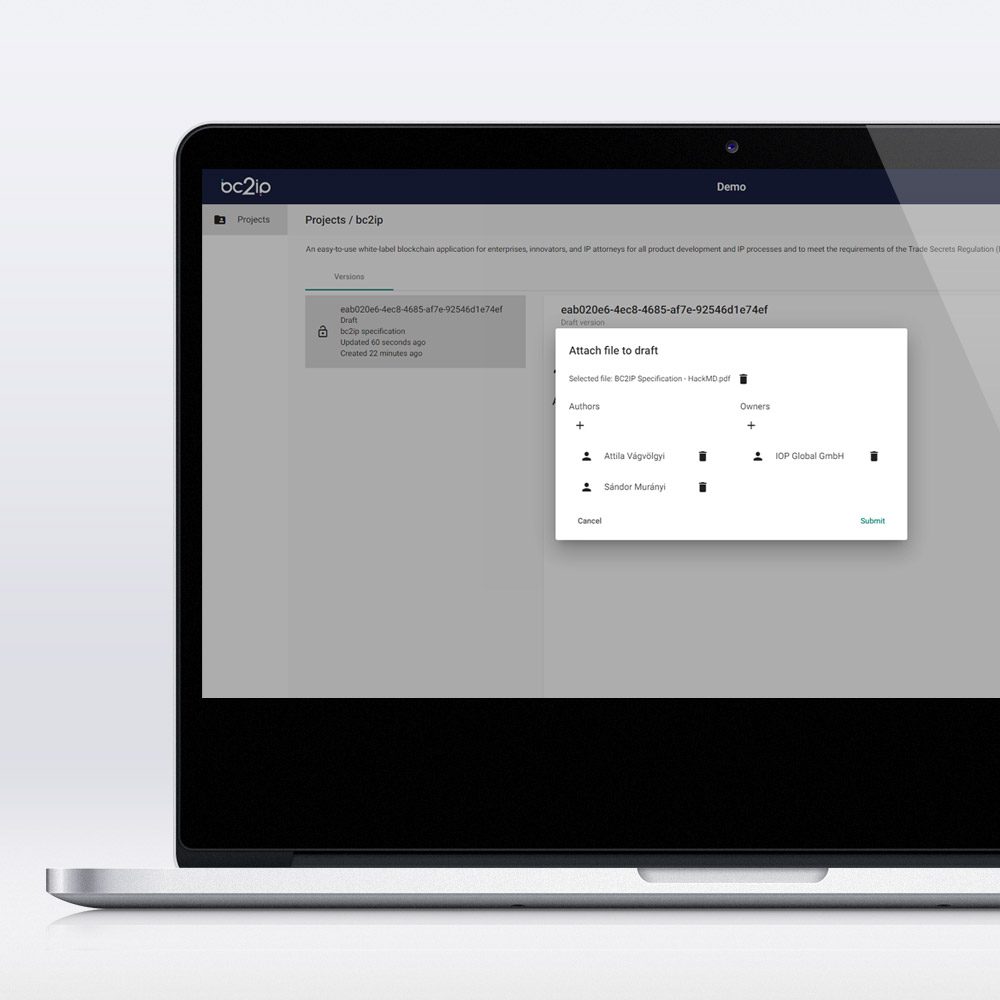
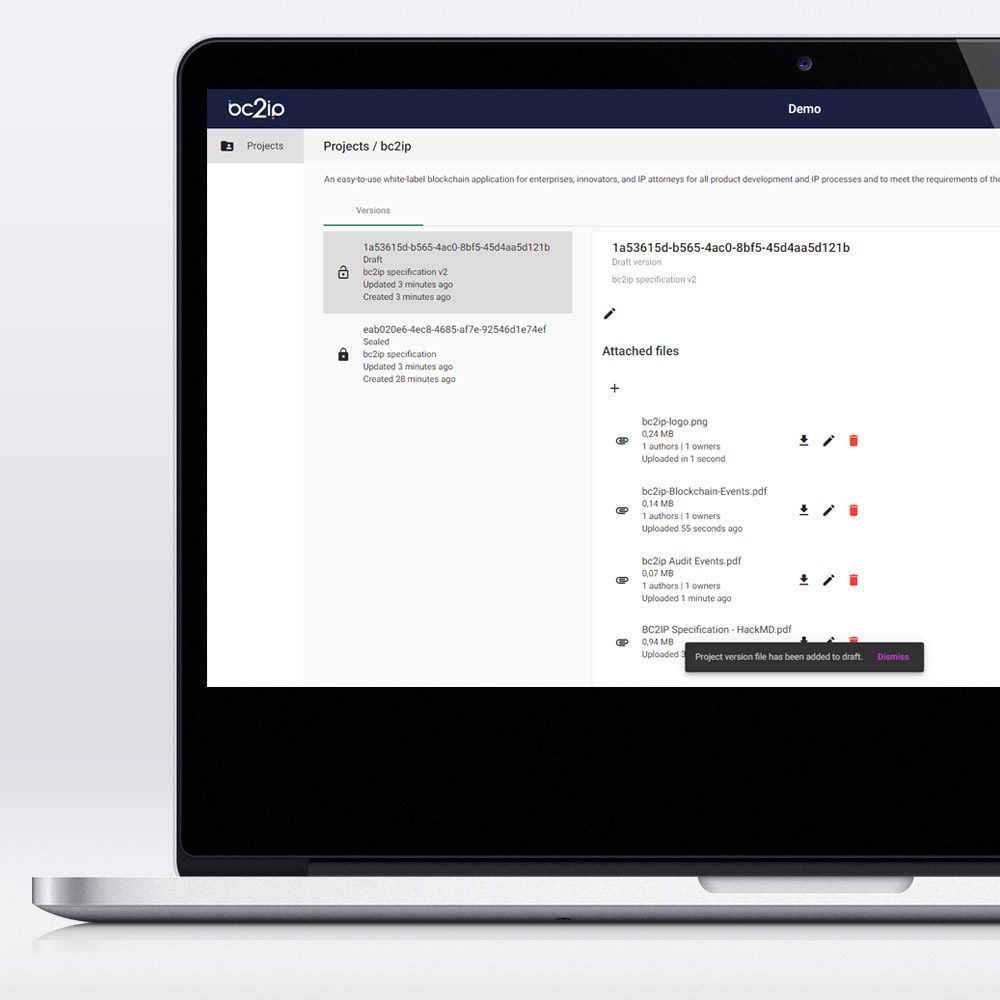
In research and development departments of companies, individual development steps can be documented using bc2ip. With the seamless documentation possible via timestamps on a blockchain, you create tamper-proof evidence and take essential steps to protect your trade secrets and copyrights, developments, and invention contributions of your employees, as well as your know-how.
.Protective measure for documenting the exchange of confidential information:
Many different use cases make the exchange of confidential and secret information necessary. bc2ip can be used as a management platform for secret information, and a documented exchange with identified participants can occur within the platform. An integration into NDAs is possible.
.Management of trade secrets:
Companies use the in-house bc2ip instance to store their internal data. Access is granted to employees only according to the "need-to-know" principle. If an employee leaves or joins the company, management can track who had access to which data, when access was granted, and from where.
.Notice and warning function:
Employees generally represent the most significant security risk for trade secrets. The daily handling of trade secrets sometimes leads to employees neglecting the importance and necessity of secure handling. A company can place a notice within the bc2ip software about the confidentiality obligations of employees in order to comply with the regular notice and warning obligations required (according to the German Trade Secrets Protection Act).
.Protection of unknown trade secrets:
The protection afforded by the German Trade Secrets Protection Act also covers information the trade secret owner may not be aware of. Using bc2ip within an R&D department helps record development processes in such a way that they can be directly attributed to the company as the secret owner at the time of their creation.
.Practical accompaniment of dynamic non-disclosure agreements:
Especially in agile development processes, non-disclosure agreements must be suitable for protecting the information available at the time of contract conclusion and subsequent data. The mandatory use of bc2ip serves to implement such a dynamic agreement practically.
.Fulfillment of assignment function:
According to the GeschGehG, Suitable secrecy measures also enable the identification of the secret owner, the so-called "assignment function". By marking the bc2ip white-label platform with the own company logo, as well as the naming of the company as the owner of the respective information, the identification of the secret owner by bc2ip is made possible.
.General data access protection:
bc2ip enables (intrinsically) the limitation of access to specific data and thus the restriction of the information flow, as well as the assignability of the previous information flow. The restriction of access and use is probably the most important measure in the context of information protection, according to GeschGehG.
.Protection of trade secrets even after an employee leaves:
Thanks to the assignment function and the possibility of complete documentation, special knowledge of an employee, e.g., regarding certain trade secrets, can be specifically named. This tamper-proof and person-specific documentation of the respective knowledge opens up the possibility of creating an effective non-disclosure agreement, even beyond the duration of an employee's employment with the company.
.Avoiding indirect infringement of trade secrets:
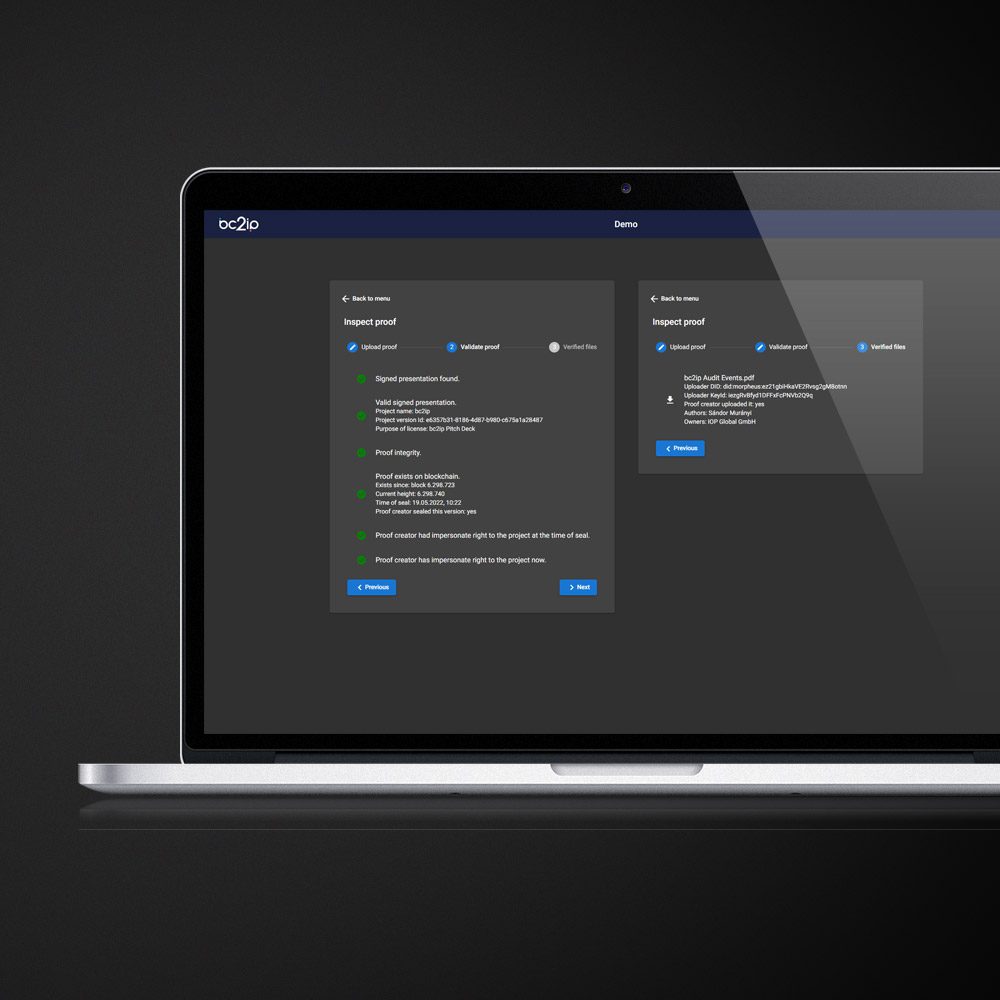
The proof inspector can prevent indirect infringement of trade secrets. An indirect breach occurs when a third party exploits a trade secret of which he must have known that the disclosing person was not authorized to disclose it. The bc2ip Proof Inspector offers the possibility to verify the authorizations of the disclosing party digitally.
.Concretization of trade secrets in (dynamic) NDAs:
NDAs require (especially in employment relationships) a concretization that the secret recipient can recognize which information is to be kept confidential. Provided that bc2ip is chosen as the means for managing confidential information of an NDA, the secrets are already concretized by using bc2ip as being subject to the NDA and thus "secret". Further warning means (e.g., associated contractual penalty) will be included if necessary.